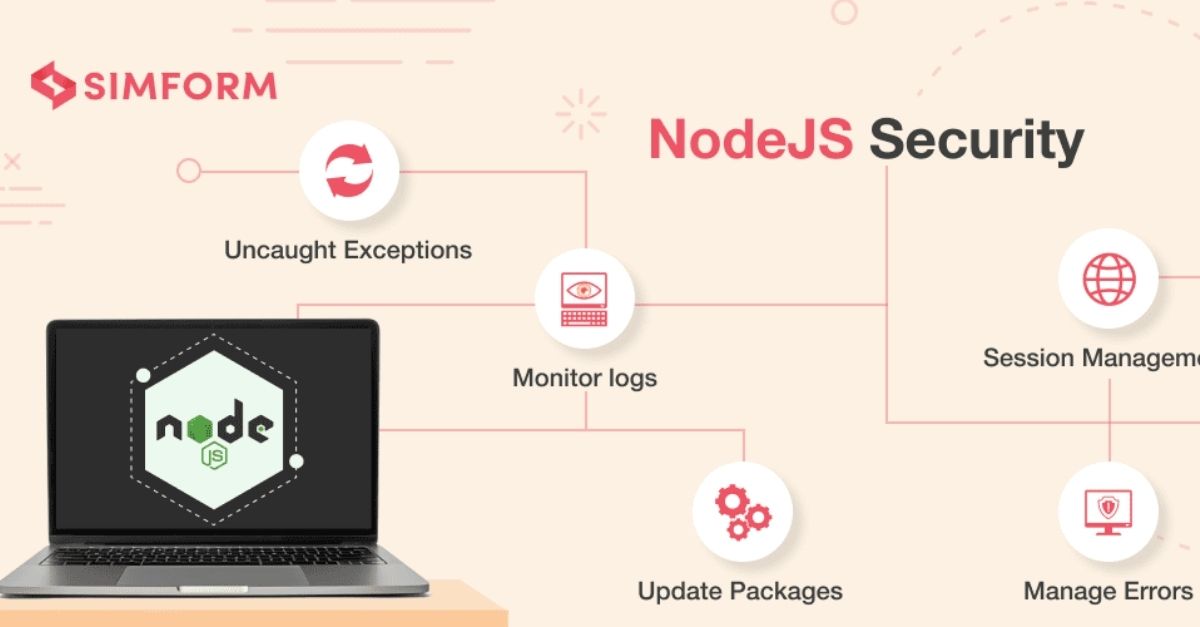
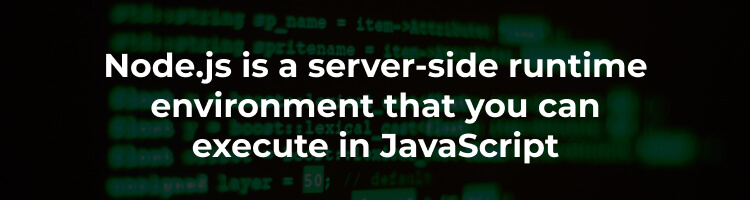
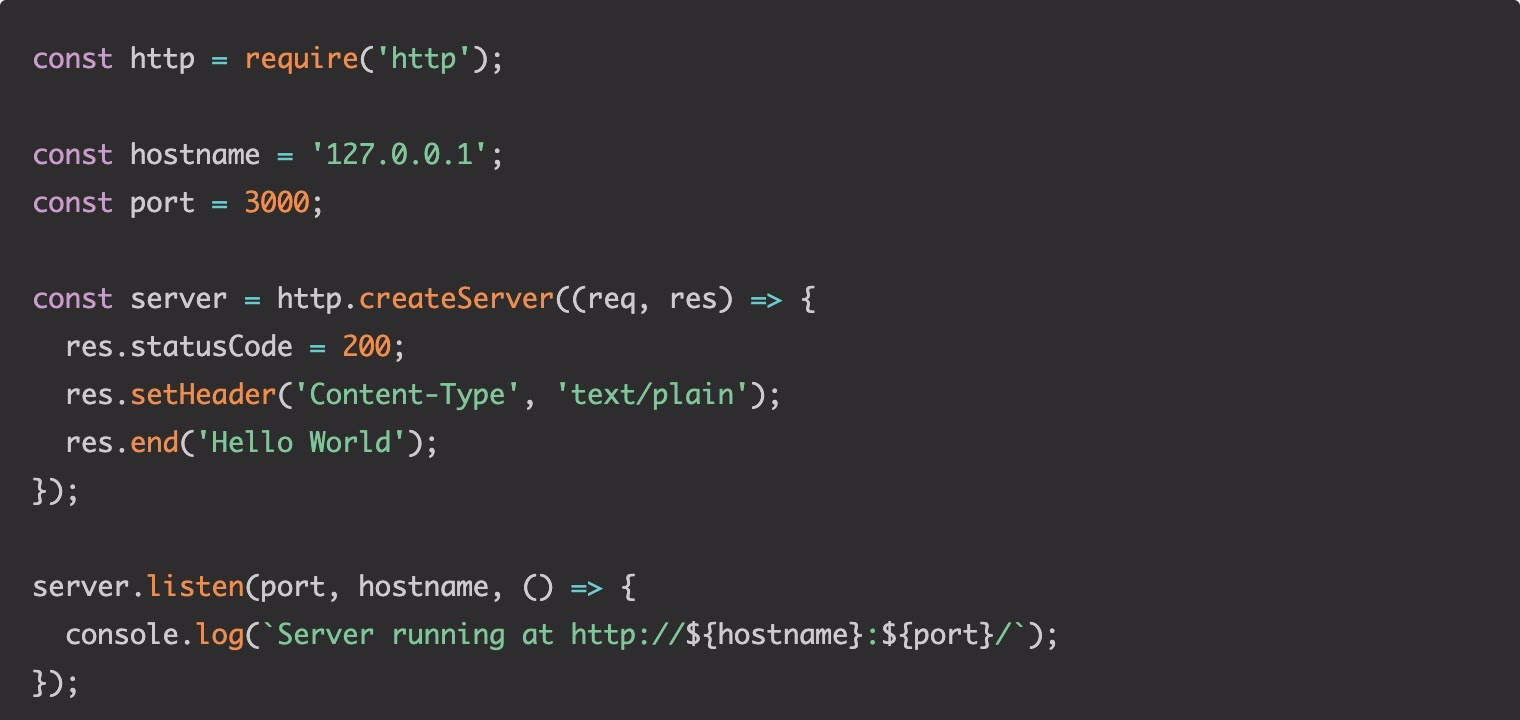
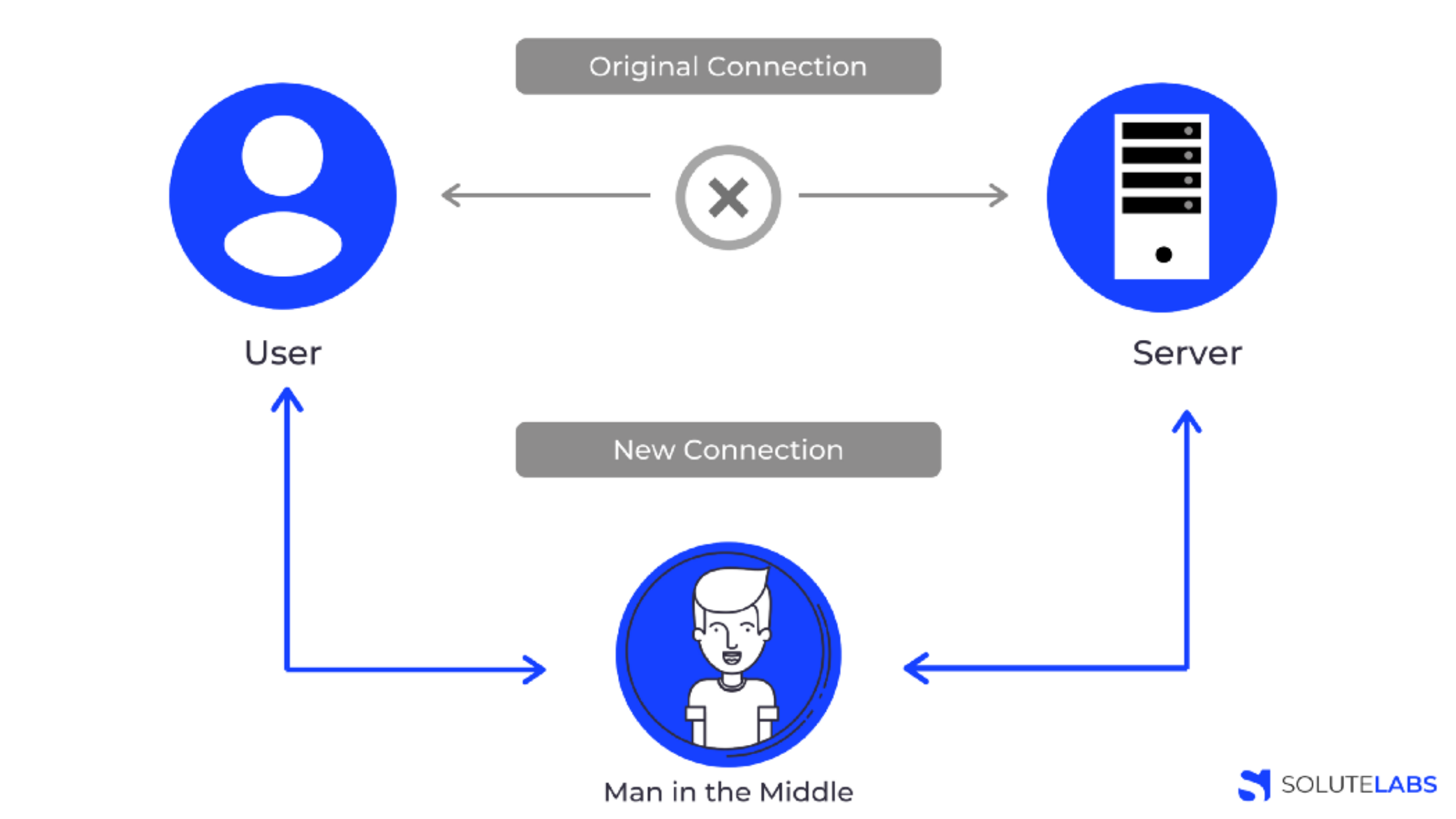
Docker node.js image comes with many vulnerabilities on Debian · Issue #787 · nodejs/docker-node · GitHub
GitHub - alexa-samples/skill-sample-nodejs-highlowgame: The high low game is a game where the player tries to guess the target number. After each incorrect guess, the player is informed if the target number is

Pentesting Node.js Application : Nodejs Application Security - Web Security Geeks - The Security Blog

Enter "Sandbreak" - Vulnerability In vm2 Sandbox Module Enables Remote Code Execution (CVE-2022-36067)