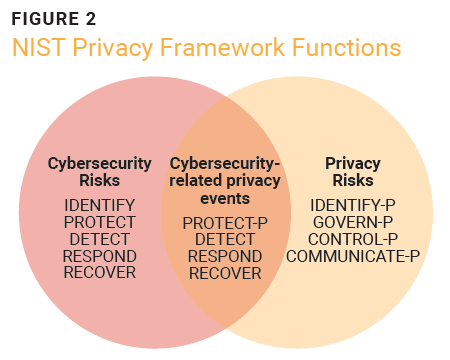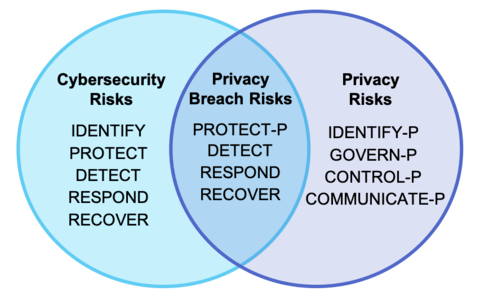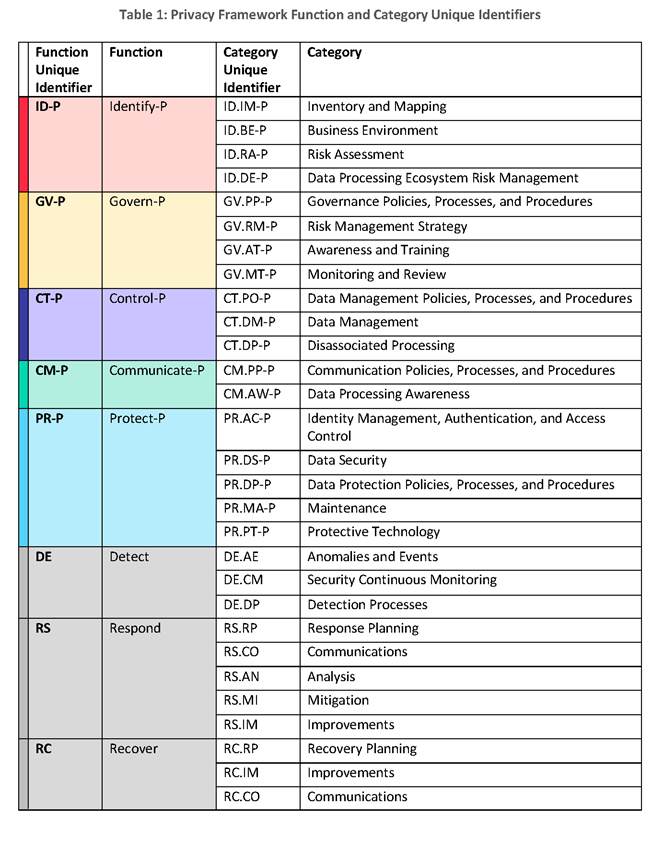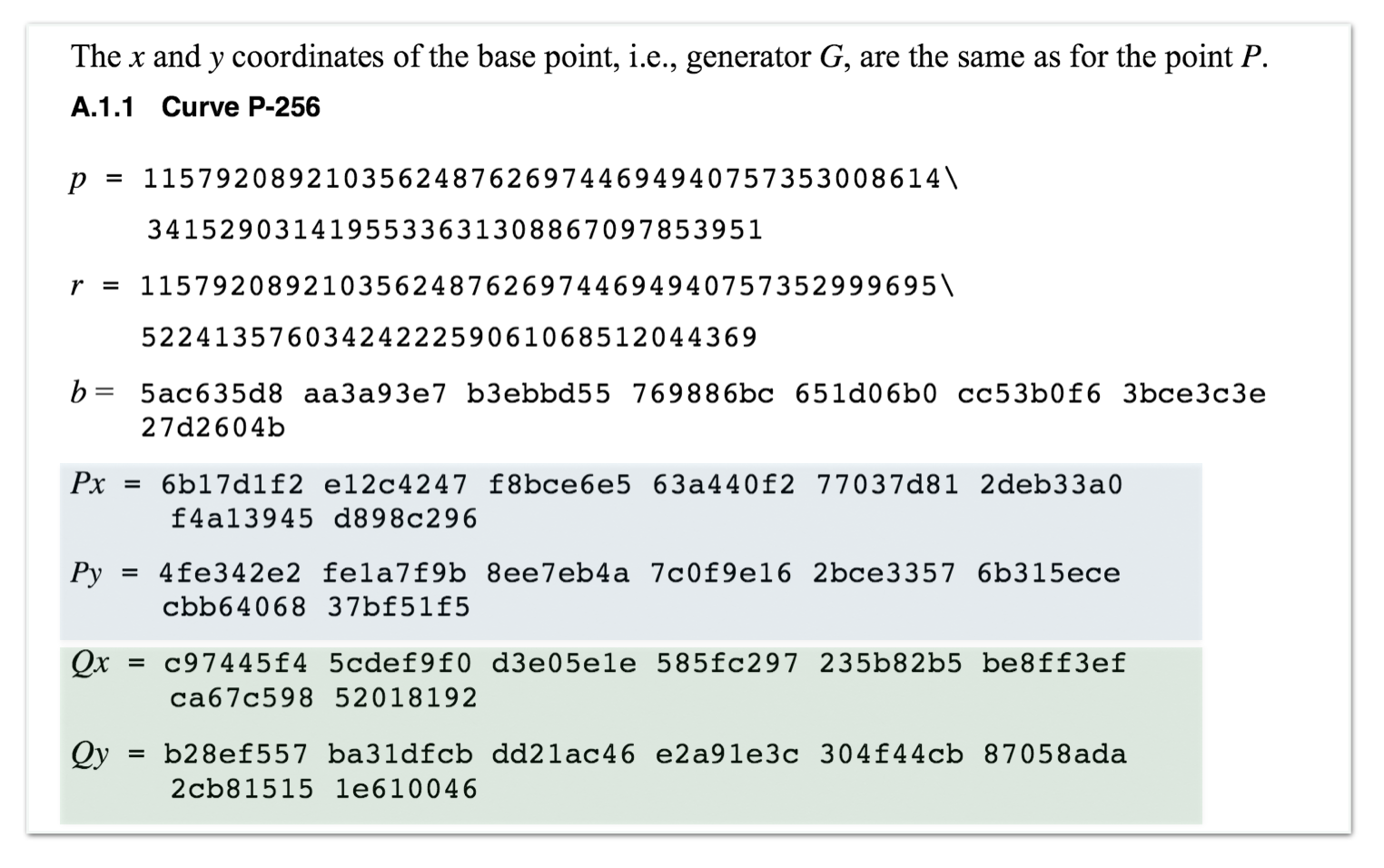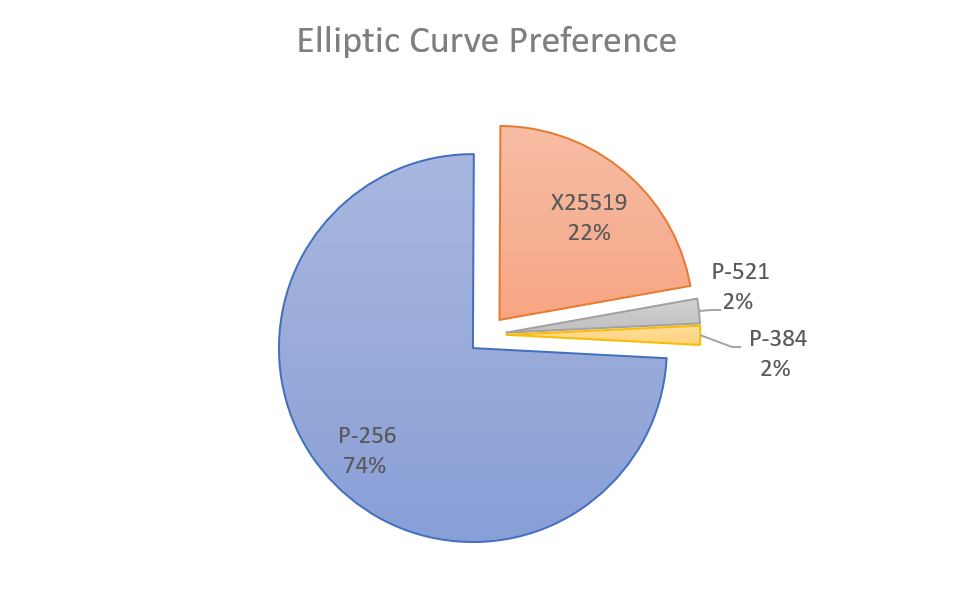
Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators

NIST Traceable Digital Convection Vacuum Gauge with Power Supply - Up to 1E-4 Torr - EQ-CVM-211-P-LD

Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators