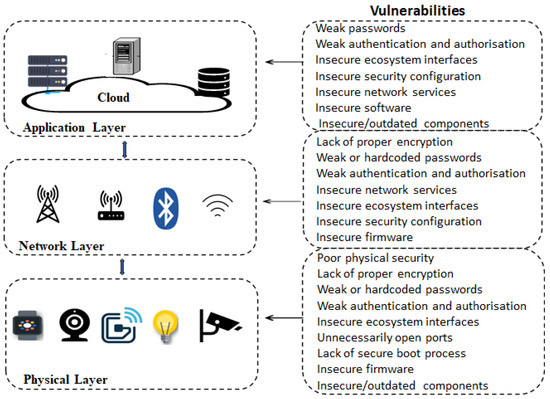
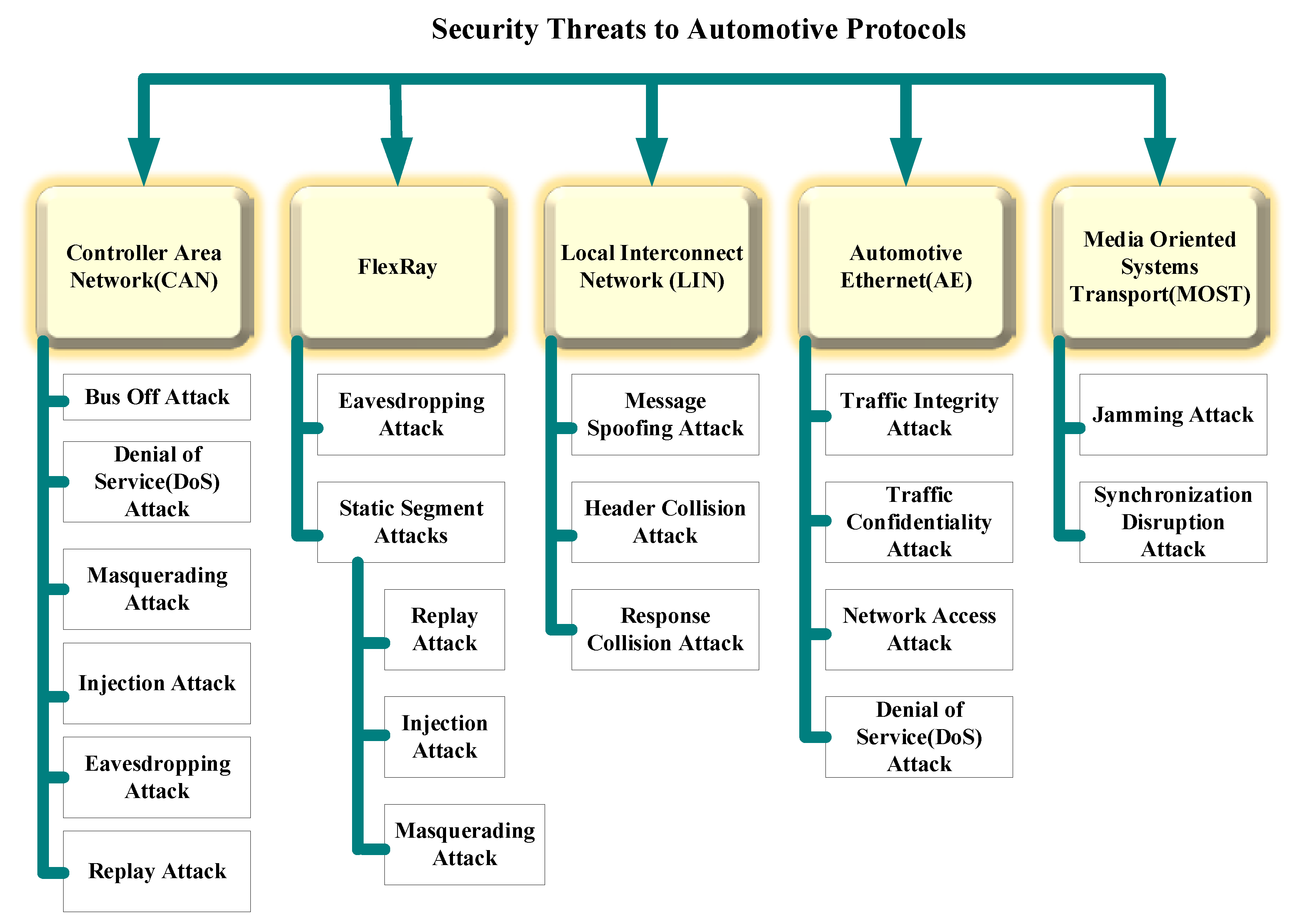
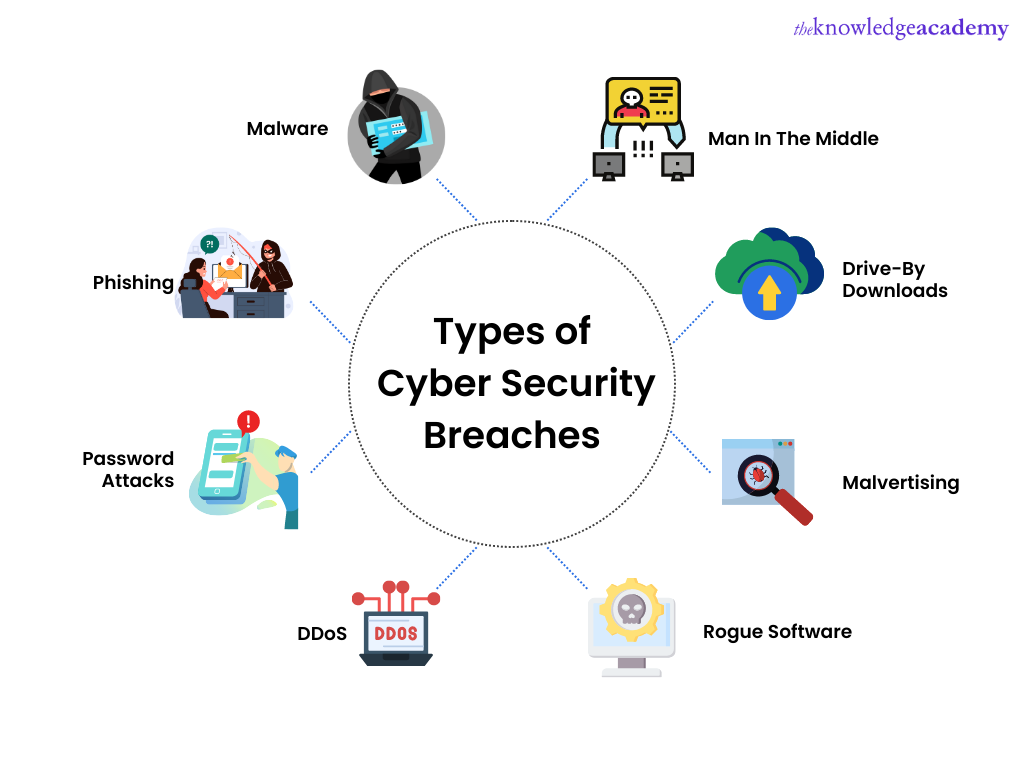
A detailed survey of denial of service for IoT and multimedia systems: Past, present and futuristic development | SpringerLink

Botnet attack detection in Internet of Things devices over cloud environment via machine learning - Waqas - 2022 - Concurrency and Computation: Practice and Experience - Wiley Online Library

Electronics | Free Full-Text | Enhancing Security on IoT Devices via Machine Learning on Conditional Power Dissipation