CS361: Introduction to Computer Security Meaning of Computer Security Confidentility Ain't Enough Commercial Security

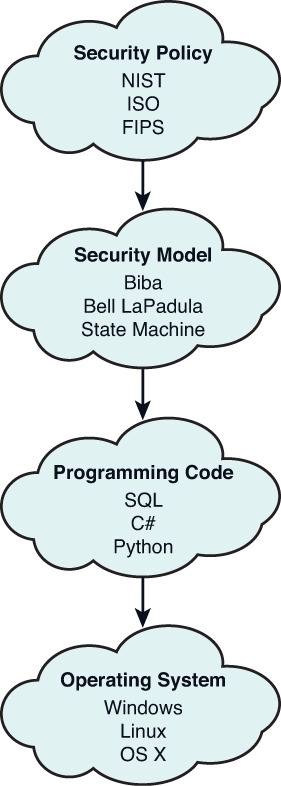
Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

What are the 5 Major Types of Classic Security Models? - Cyber Security Certifications, Cyber Security Consulting, RogueLogics

Managing Information Confidentiality Using the Chinese Wall Model to Reduce Fraud in Government Tenders | Semantic Scholar

Which of the following models describe how subjects and objects must be created and deleted? - Skillset

Security Models Pt 3 Clark-Wilson, Brewer and Nash, Graham-Denning (CISSP Free by Skillset.com) - YouTube
▻ Bell-LaPadula model ▻ Biba model ▻ Chinese Wall model ▻ (Clark-Wilson model) ▻ Demonstrate how security policies can