Pass-the-Hash Is Dead: Long Live LocalAccountTokenFilterPolicy | by Will Schroeder | Posts By SpecterOps Team Members
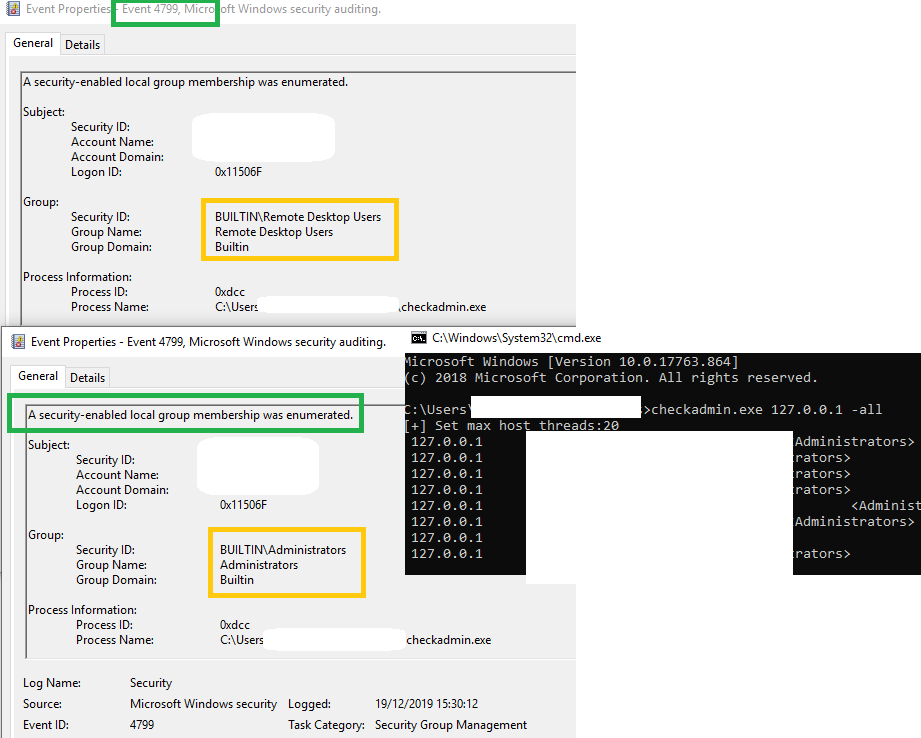
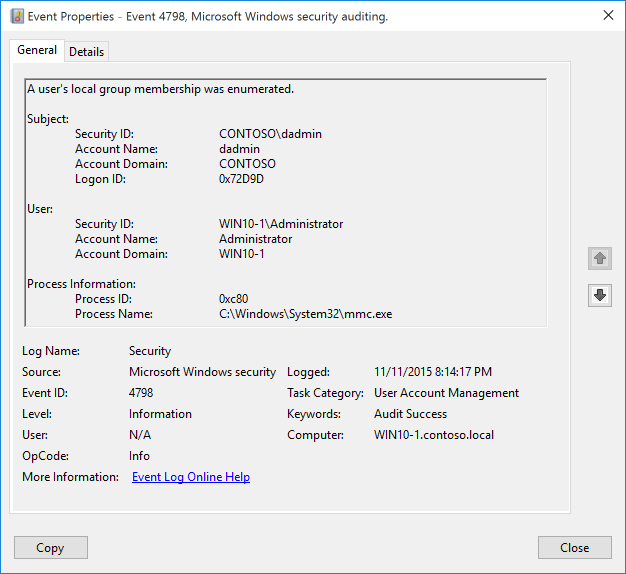
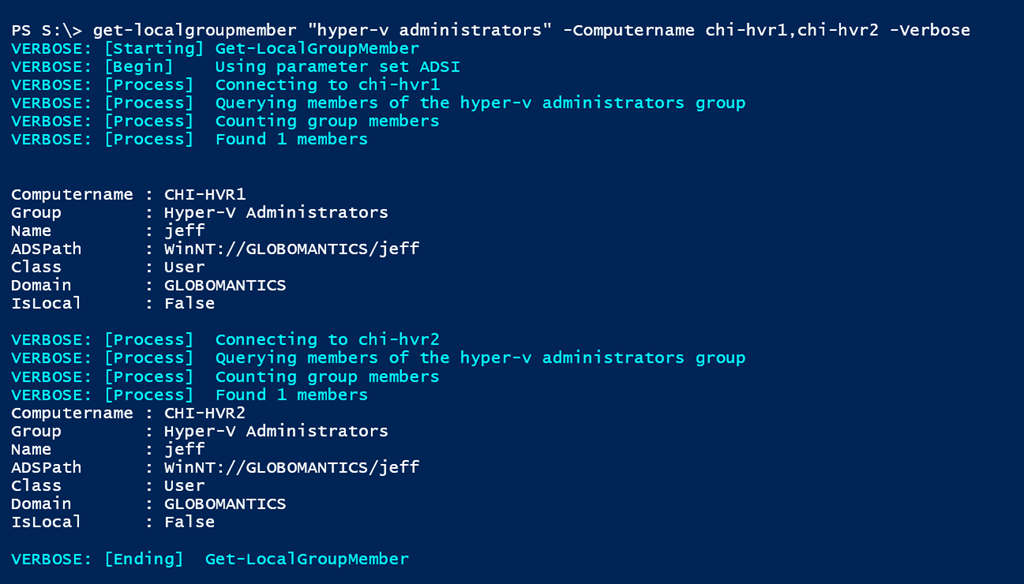
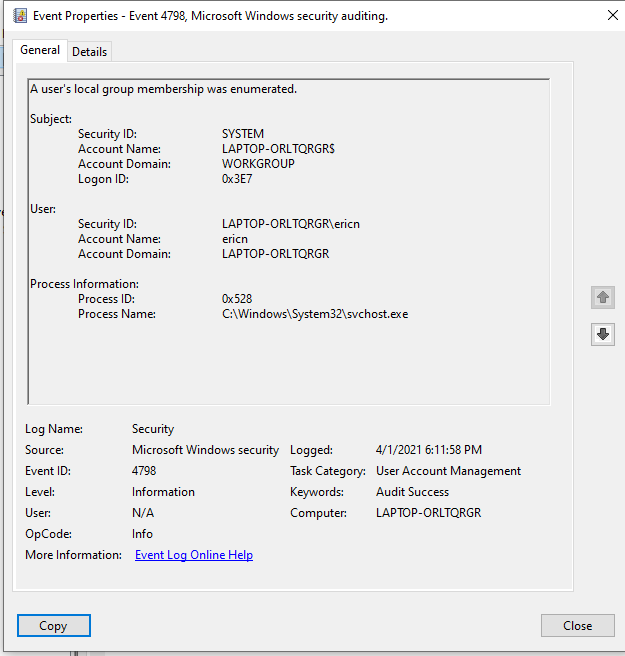
Samir on Twitter: "the cool thing about those 2 newly introducted MS security eventid 4799, 4798 is that they will capture any local group/user discovery attempts even if done via winapis, below
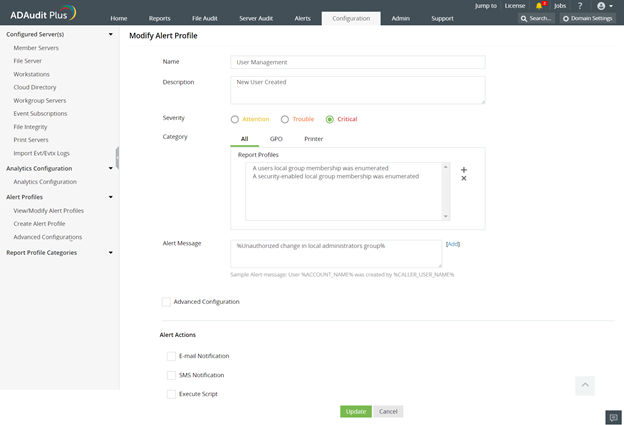
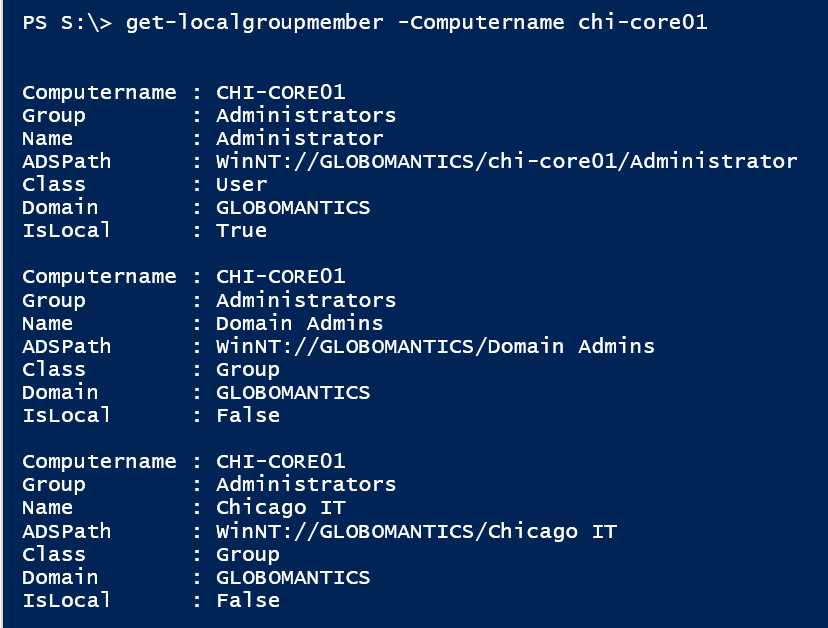
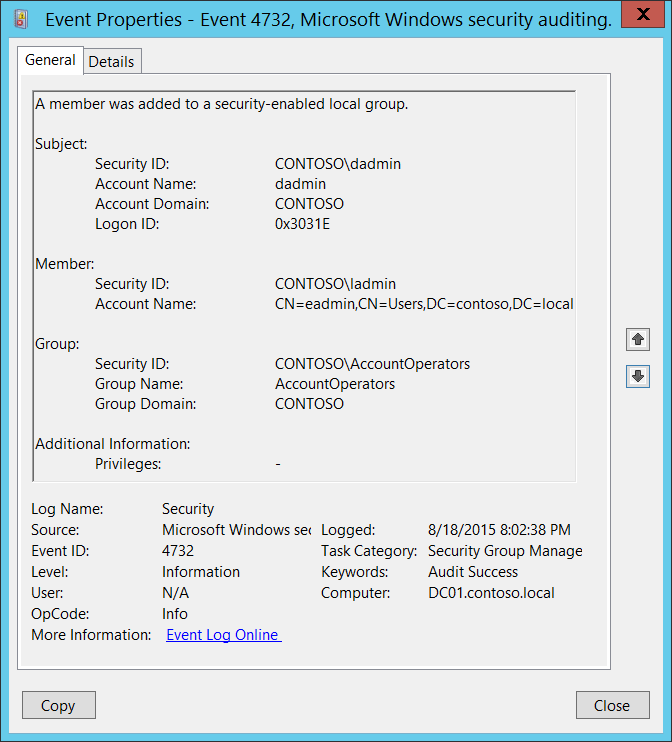
Secure workstations by monitoring and alerting on membership changes in the local Administrators group, Part 2 - ManageEngine Blog

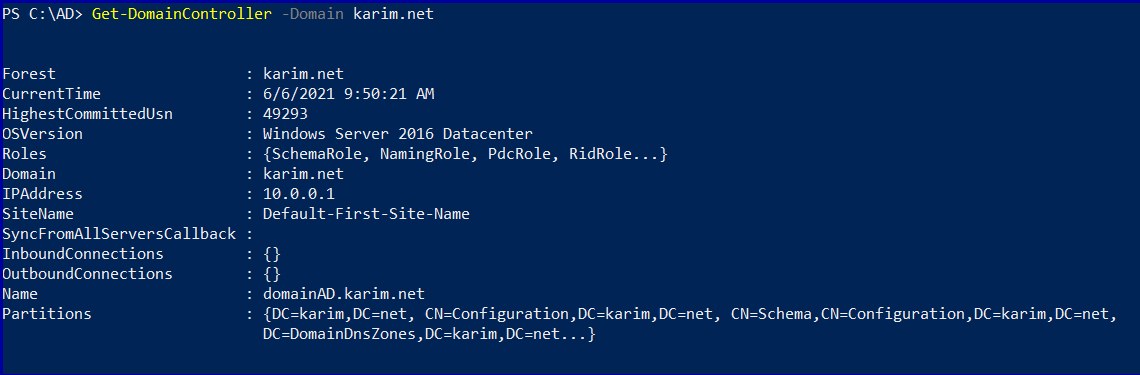
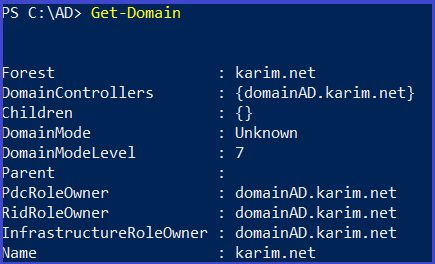
Active Directory Enumeration detected by Microsoft Security solutions | by Derk van der Woude | Medium

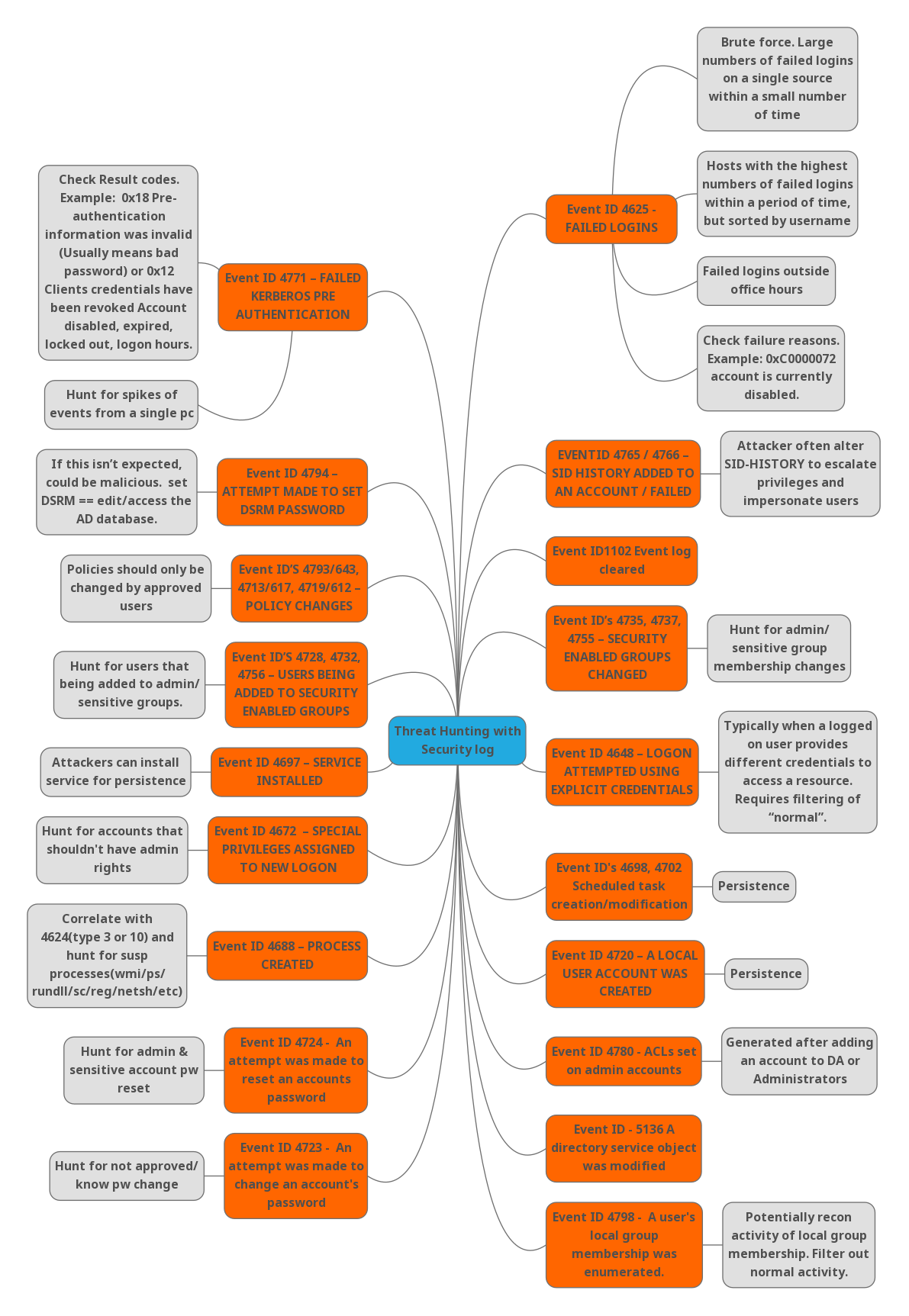
I-SECURE CO., LTD. - 🔥 สูตรวิเคราะห์ Windows Event Log สำหรับ Threat Hunter และ Incident Responder 🔥 | Facebook